Good pictures
Approximately 11 million web-exposed servers are vulnerable to a recently discovered vulnerability that could allow attackers to enter affected networks. Once they're in, attackers compromise the integrity of SSH sessions, which form the linchpin for administrators to securely connect to computers in the cloud and other critical environments.
Terrapin, named Vulnerability, came to light two weeks ago in a research paper published by academic researchers. Tracked as CVE-2023-48795, when attackers use an adversary-in-the-middle attack (AitM, abbreviated as man-in-the-middle or MitM), the researchers proposed an attack that repositions itself on the same local network and secretly intercepts communications, compromising both the recipient and the sender. Identification can also be taken.
In those cases, Terrapin allows attackers to alter or corrupt the information sent in the SSH data stream during the handshake—the initial connection stage when both parties negotiate the encryption parameters used to establish a secure connection. Thus, Terrapin represents the first practical cryptographic attack targeting the integrity of the SSH protocol. It targets BPP (Binary Packet Protocol), which is designed to ensure that AitMs cannot add or drop messages exchanged during a handshake. This is Prefix truncation The attack works when implementations support “ChaCha20-Poly1305” or “CBC with Encrypt-then-MAC,” cipher modes, which were detected on 77 percent of SSH servers at the time the paper was published.
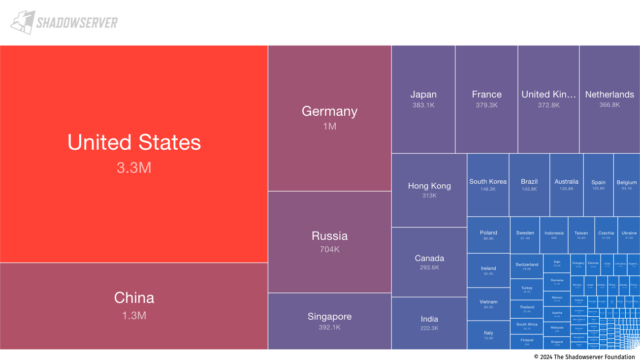
A web-wide scan performed on Tuesday, the last day such data was available at the time of reporting, found more than 11 million IP addresses exposing an SSH server to be vulnerable to Terrapin. Almost a third of those addresses, 3.3 million, reside in the United States, followed by China, Russia, Germany, Russia and Singapore. All unconnected implementations monitored by Shadowserver support the required cipher methods.
Shadow Server
Only 53 of the vulnerable instances relied on implementations of AsyncSSH, which is currently the only implementation known to be seriously affected by Terrapin. Two vulnerabilities found in AsyncSSH allowed Terrapin to inject or drop packets or impersonate installed shells. AsyncSSH addresses those two vulnerabilities, tracked as CVE-2023-46445 and CVE-2023-46446, in addition to CVE-2023-48795, a Terrapin vulnerability affecting the SSH protocol. Most AsyncSSH users seem to have installed patches.
The need for AitM status and the lack of currently known practical attacks by Terrapin are important mitigating factors, which some critics say have been lost in some news coverage. At this point, since the patches were widely available one to two weeks ago, there are some good reasons not to fix the protocol flaw now.
“This attack requires quite a bit of complexity in that MitM is necessary, so in our view it will limit practical use to more targeted attacks,” Shadowserer researcher Piotr Kijewski wrote in an email to Ars. “So it's unlikely to be subject to mass exploitation. However, the sheer volume of vulnerable events suggests that this vulnerability will be with us for years to come and in some specific cases it will be attractive.”
Although Terrapin is unlikely to be widely exploited, it has the potential to be used in targeted attacks by sophisticated attackers, such as those supported by nation-states. While earlier versions of AsyncSSH were the only known implementation vulnerable to practical terrapin attacks, researchers spent some time analyzing other implementations. Adversaries with more time, resources, and motivation can identify other vulnerable implementations.
Kijewski listed the top 50 banners displayed by vulnerable IP addresses:
- number of servers_software
- openssh_7.4 2878009
- openssh_7.6p1 956296
- openssh_8.2p1 802582
- openssh_8.0 758138
- openssh_7.9p1 718727
- openssh_8.4p1 594147
- openssh_8.9p1 460595
- openssh_7.2p2 391769
- openssh_7.4p1 320805
- openssh_8.5 316462
- openssh_9.3 298626
- openssh_8.7 219381
- openssh_6.7p1 156758
- openssh_9.2p1 141010
- openssh_6.6.1p1 136489
- openssh_9.0 112179
- openssh_6.6.1 105423
- dropbear_2020.80 93154
- openssh_8.8 88284
- openssh_7.5 76034
- aws_sftp_1.1 75157
- openssh_9.0p1 70305
- openssh_8.2 59887
- openssh_7.9 59301
- Drop Bear 51374
- openssh 35408
- openssh_7.2 34494
- openssh_7.8 33955
- dropbear_2020.81 28189
- openssh_9.5 27525
- openssh_9.1 26748
- openssh_8.1 23188
- lancom 22267
- openssh_6.4 18483
- openssh_8.4 18158
- openssh_8.9 17310
- openssh_7.6 17235
- openssh_for_windows_8.1 17150
- openssh_for_windows_7.7 15603
- openssh_8.6 14018
- openssh_6.9 13601
- openssh_9.4 12802
- dropbear_2022.82 12605
- dropbear_2022.83 12036
- openssh_7.7 11645
- openssh_for_windows_8.0 11089
- openssh_7.3 10083
- mod_sftp 9937
- openssh_8.3p1 9163
- Cisco-1.25 8301
Patching Terrapin is not straightforward because of the multiple implementations involved and the need to patch apps running on both the admin client and server. The researchers listed the following implementations as vulnerable and included links to patches when available. Asterisks indicate application developers contacted prior to publication of the research paper:
| Implementation | Affected versions | Linked Version(s) |
|---|---|---|
| AsyncSSH* | 2.14.1 and earlier | 2.14.2 |
| Bitwise SSH* | 9.31 and earlier | 9.33 |
| ConnectBot* | 1.9.9 and earlier | 1.9.10 |
| CrushFTP | 10.5.6 and earlier | 10.6.0 |
| SSH Hurricane* | 2.3.2 and earlier | 2.3.4 |
| drapery* | 2022.83 and earlier | To be freed |
| Erlang/OTP SSH* | OTP 26.2 and earlier OTP 25.3.2.7 and earlier OTP 24.3.4.14 and earlier |
OTP 26.2.1 OTP 25.3.2.8 OTP 24.3.4.15 |
| FileZilla client | 3.66.1 and earlier | 3.66.4 |
| Golang x/crypto/ssh* | 0.16.0 and earlier | 0.17.0 |
| JSch (Fork)* | 0.2.14 and earlier | 0.2.15 |
| libssh* | 0.10.5 and earlier 0.9.7 and earlier |
0.10.6 0.9.8 |
| libssh2* | 1.11.0 and earlier | To be freed |
| Maverick Legacy* | 1.7.55 and earlier | 1.7.56 |
| Maverick Synergy* | 3.0.21 and earlier (hotfix) 3.0.10 and earlier (OSS) |
3.0.22 3.1.0-snapshot |
| MobaXterm | 23.5 and earlier | 23.6 |
| Noah | 11.7 and earlier | 11.8 |
| OpenSSH* | 9.5 / 9.5p1 and earlier | 9.6 / 9.6p1 |
| paramico* | 3.3.1 and earlier | 3.4.0 |
| phpseclib | 3.0.34 and earlier 2.0.45 and earlier 1.0.21 and earlier |
3.0.35 2.0.46 1.0.22 |
| PKIX-SSH* | 14.3 and earlier | 14.4 |
| ProFTPD* | 1.3.8a and earlier | 1.3.8b |
| putty* | 0.79 and earlier | 0.80 |
| rush* | 0.40.1 and earlier | 0.40.2 |
| SecureCRT* | 9.4.2 and earlier | 9.4.3 |
| SFTP gateway | 3.4.5 and earlier | 3.4.6 |
| SFTPGo | 2.5.5 and earlier 2.4.5 and earlier |
2.5.6 2.4.6 |
| ssh2* | 1.14.0 and earlier | 1.15.0 |
| ssh* | 0.37.0 and earlier | 0.38.0 |
| Tera period* | 5.0 and earlier 4.107 and earlier |
5.1 4.108 |
| thrush* | 0.34.0 and earlier | 0.35.1 |
| TinySSH | 20230101 and earlier | 20240101 |
| send | 5.10.3 and earlier | 5.10.4 |
| Win32-OpenSSH* | 9.4.0.0p1-beta | 9.5.0.0p1-beta |
| WinSCP | 6.1.2 and earlier | 6.2.2 Beta |
| XShell 7* | Build 0142 and earlier | Create 0144 |
As explained earlier, there is little cause for mass alarm. Terrapin is not a Citrix bleed, CVE-2022-47966, MoveID, CVE-2021-22986, or CVE-2023-49103, or CVE-2021-22986, which are some of the most exploited vulnerabilities of 2020. Millions of servers. So far, there are no known reports of Terrapin patches causing side effects. Admins better patch it soon.

“Friend of animals everywhere. Devoted analyst. Total alcohol scholar. Infuriatingly humble food trailblazer.”